I just received an email supposedly from “[email protected]” claiming that LogMeIn.com is moving to 1024 bit encryption from 128 bit. I am an avid user of LogMeIn and love their service. This seemed a bit odd to me so I decided to investigate this a bit further. As it turns out, it is a Phishing Scam that is now trying to get users to put in their LogMeIn information. (I have covered Phishing scams before. See posts #1, #2 and #3.) This is a very big concern to any LogMeIn users since this essentially gives the scammer access to any accounts in the LogMeIn user’s profile. The good news is, though, that it would be seemingly difficult for the scammer to actually access a computer in said account because you also need to have the security credentials of the computer that is being accessed.

I wanted to be sure that people understand what this phishing scam looks like so that they know to AVOID it. Here are the details:
The Email
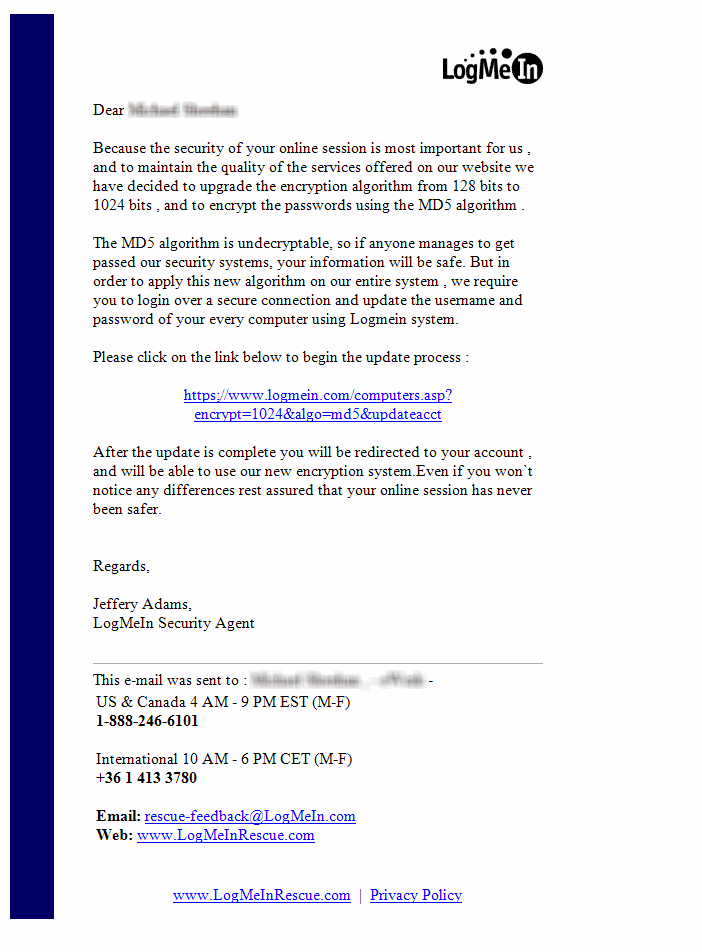
I have included the text of the email below in order for Search Engines to pick up the content. Below that is also the image of the email that I received.
Dear [USER FIRST & LAST NAME]
Because the security of your online session is most important for us , and to maintain the quality of the services offered on our website we have decided to upgrade the encryption algorithm from 128 bits to 1024 bits , and to encrypt the passwords using the MD5 algorithm .
The MD5 algorithm is undecryptable, so if anyone manages to get passed our security systems, your information will be safe. But in order to apply this new algorithm on our entire system , we require you to login over a secure connection and update the username and password of your every computer using Logmein system.
Please click on the link below to begin the update process :
https;//www.logmein.com/computers.asp?encrypt=1024&algo=md5&updateacct
After the update is complete you will be redirected to your account , and will be able to use our new encryption system.Even if you won`t notice any differences rest assured that your online session has never been safer.Regards,
Jeffery Adams,
LogMeIn Security Agent
________________________________________
This e-mail was sent to : [USER FIRST & LAST NAME] , – [COMPANY] –
US & Canada 4 AM – 9 PM EST (M-F)
1-888-246-6101International 10 AM – 6 PM CET (M-F)
+36 1 413 3780Email: [email protected]
Web: www.LogMeInRescue.comwww.LogMeInRescue.com | Privacy Policy
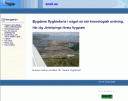
Here is what the email actually looked like on my computer (click to view it larger):
Some interesting things to note on this email. First, it looks pretty legitimate. The sentence structure isn’t bad but there are a few “mistakes” that I picked up on:
- “…important FOR us…” should really read “…important TO us…”
- Note the space and comma on that first phrase as well. It’s common that this happen in phishing emails. These space and comma and periods are prevalent throughout the email. There are other instances where there are no spaces between periods and also there is a “backwards” apostrophe after “won’t” which, to me, suggests a foreign character set.
- “…on our website we…” – there should really be a comma after “website” and there are many other instances where there should or should not be commas.
- “MD5 algorithm” – MD5 encryption is used with Software in order to verify that a file has not been changed or altered. Typically, an MD5 checksum is provided in conjunction with a file to compare the values. More info on MD5 can be found here. I viewed the statement of “encrypt the passwords using the MD5 algorithm” to be misleading and most likely erroneous.
- “…won’t notice any differences…” – scary statement. Yes, you won’t notice any differences until the scammer goes into your account and takes it over. Then you WILL notice a difference.
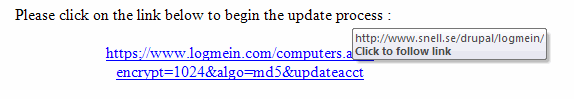
- The link for the URL to “begin the update process” is not what it appears. If you look at the text, it says “https;//”. Note that there is NOT a colon but rather a semicolon there which is NOT a valid URL. Also, in Outlook 2007 (and other email programs), when you mouse over the address, you get a different ACTUAL address, namely: “http://www.snell.se/drupal/logmein/”. See image below:

The Phishing Site
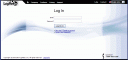
Assuming you have foolishly gone to the site, you are presented with a very valid looking “LogMeIn” login page. Even the security certificate that loads looks valid (it IS the LogMeIn certificate, but used on the WRONG domain). If your browser is good, you will get a warning about the Security Certificate not being for the site that you are on. Each browser seems to do it differently. IE notifies you with a ribbon at the top and does not load all of the images. Firefox displays a prompt about an invalid domain for the site you are on. Heed those warnings! Here is what the loaded site looks like:
This is a very good copy of the site actually. It even draws the images from “https://secure.logmein.com” (but that is part of the reason why you get secure Certificate warnings). If you start digging around in the HTML, you will see that the Form Action does not post to LogMeIn. A quick look at the code shows that it posts to the phishing site:
<form name=”login_pw” method=post action=”http://www.snell.se/drupal/logmein/login.php”>
Just to test to see what happens on that form, I entered in some TEST data (not a valid LogMeIn account) and submitted the form. The result? The form simply reloaded. I would think that the information is now logged in a Database somewhere for the scammer to use and test out.
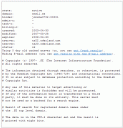
I did some quick research on the domain and found the following information.
WHOIS info:
The site above the “/logmein/”:
And the level above that (the root level of www.snell.se):
It looks like the domain is hosted on a Swedish provider called “Oderland Webbhotel” located at: http://www.oderland.se/webbhotell/.
That is about the extent of the research that I did. It is a legitimate FAKE and a definite PHISHING SCAM.
I will be notifying LogMeIn of this. I do see that they know and have posted it on their forums. However, you can only access this announcement if you log in to your account. It might be worth for them to get it somewhere outside of that and on their public site. If you feel that this is important, be sure to pass this information on and DIGG this post.
HTD says: Once again, watch out for Phishing Scams! Only open sites from emails where you are absolutely positive they are legit.


8 comments
Tygra
Great post and analysis of the email. I’m using your post to help educate my company about such emails.
Duereermire
Hello guys!
New here and just want to welcome you.
____________________________________
Music Blog
Harry
This is a nice post about colon cleansing and how to remove this type of problem of colon..
Thanks for such an important article.
Harry
This is a nice post about colon cleansing and how to remove this type of problem of colon..
Thanks for such an important article.
Michael
@ Justin,
Thanks for the comment. I think this is starting to make rounds. I have notified LogMeIn (no response from them yet but they did post to their forum a few days ago about the issue).
If you haven’t already, please DIGG this post in order to raise the awareness of this security issue.
Thanks,
HTD
hightechdad
@ Justin,
Thanks for the comment. I think this is starting to make rounds. I have notified LogMeIn (no response from them yet but they did post to their forum a few days ago about the issue).
If you haven’t already, please DIGG this post in order to raise the awareness of this security issue.
Thanks,
HTD
Justin Gargano
Our company just got hit with this about an hour ago.
-Justin
Justin Gargano
Our company just got hit with this about an hour ago.
-Justin