I’m sure that many of you have heard of the Find My iPhone service for MobileMe that helps you locate missing iPhones or iPads. Or the equivalent on Windows Mobile phones called My Phone. And I’m sure you know about LoJack that helps you locate stolen cars. LoJack also offers a service for computers as well, for a price. There are other offerings that help you locate lost or stolen laptops out there too, but most of them are expensive. For me, it’s a bit easier to justify spending a little bit on a service like MobileMe (which does a lot more than just the “Find My iPhone” service and is good for multiple devices), and it is a lot easier to lose or have a phone stolen. Laptops are a little trickier in that they are bigger and don’t usually have built-in GPS’s or location services.
But today I came across (actually using StumbleUpon) an Open Source project called “Prey” which has taken the difficulty of setting up and configuring a behind-the-scenes service that lets you locate you lost or stolen laptop. The service is FREE and works on multiple platforms (Linux, Windows and MacOS).
Some of the highlights of the features are:
- Geo-location Aware – the Prey developers have created a way to triangulate the location of your stolen or lost laptop (assuming it’s on, of course, and connected to the internet) based on publically indexed WiFi hotspots.
- Wifi Autoconnect – this innovative feature detects if your laptop is connected to an active network connection and if it isn’t, it will try to connect to a nearby open WiFi access point.
- Lightweight – the developers coded the Prey application in bash which, according to their site, means that it has virtually no dependencies.
- Modular – Prey has a variety of different functions or modules. Read on to find out some of the different items that can be configured.
- Strong Reporting – you can configure the types of reports you get from your laptop like running programs, recently modified files, active connections, screenshots of the active desktop, and even a webcam capture.
- Alerting – you can configure Prey to pop up messages on your laptops screen, change your desktop picture (Mac/Linux), send out an alarm sound or speak an alert.
- Auto Updating – once you install Prey, you can forget about it. It will update itself (if you want it to) to the latest version automatically.
How Prey Works
It’s a pretty simple concept actually. Prey runs in the background of your computer. At predefined times (you can configure it to check every 5 minutes or 55 minutes in 5 minute increments) it wakes up and checks a unique URL for a status code. If it finds that code, it goes back to sleep. It will continue to do this repeatedly.
However, it order for Prey to work, it needs to have one of two configurations: 1) Prey & Control Panel or 2) Prey Standalone. The easiest way to do work with Prey is to use the Control Panel option which I outline below. The Standalone version was how Prey was originally launched.
Installation is pretty straight forward so I won’t go into it. I do recommend using the Control Panel version. Just don’t be confused by the name “Control Panel” because it doesn’t put anything in your system’s Control Panel. “Control Panel” actually refers to a portal where you can view and configure your devices. Each account that you register can have up to 3 devices per email address.
Setting Up and Using Prey
Use the installer to set up Prey. You can download it from the homepage. On either the Mac or PC (I didn’t test Linux), you will be walked through a wizard to set up your computer. The first time through, you will want to create a new account on the Prey Project website. Other times through for other laptops, you can just sign in with your pre-configured account.
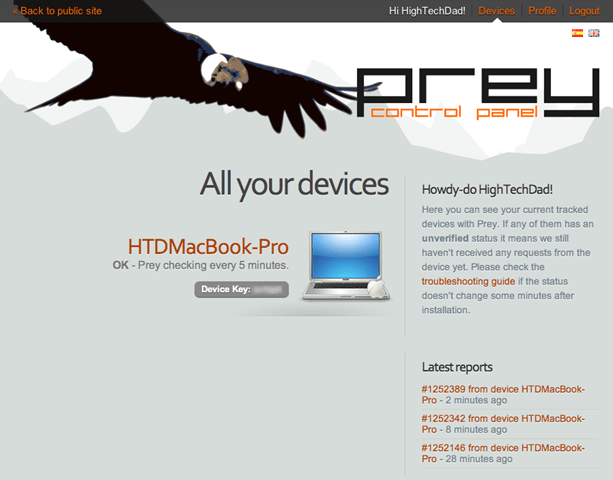
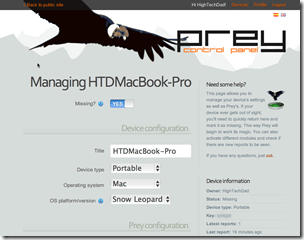
I had signed up and then went through the installation wizard. My system information was preconfigured. You can see the fields below. Also each device gets a unique key. Note the toggle at the top titled “Missing”. When your laptop is stolen or lost, you simply log into PreyProject.com and flip that toggle and Prey will start working based on your configuration (see mine below).
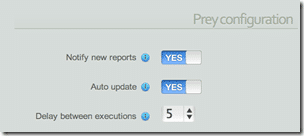
You can be notified when there is a new report (comes via email), set Prey to auto update and configure the delay between connection/reporting sessions.
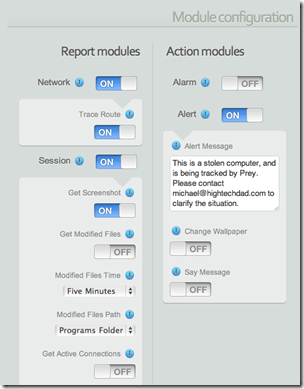
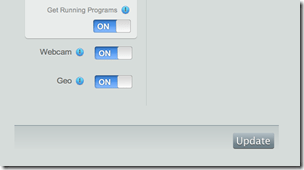
Below are some of the configuration modules. Reporting can get network, traceroute, capturing session information (screenshots, modified file list, active connections, running programs), webcam shot, and the geo-location. You can also configure types of actions can take place on your laptop including setting off an audible alarm, displaying a prompt on the screen, changing the wallpaper (Mac/Linux) and speaking a message (Mac/Linux).
So to test out Prey, I set my laptop to “Missing” via the website. Within 20 minutes, I received an email saying there was a report for me to look at. (Later, for the screenshot above, I set the interval to 5 minutes to see how well it worked.)
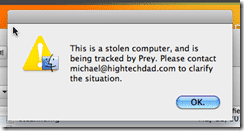
First, I received an alert on my Mac (I didn’t set any other Alert notifications):
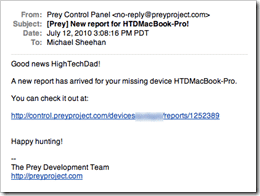
I then received my email:
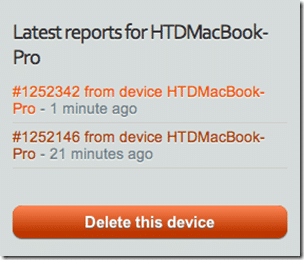
I then clicked through the email to receive my report. Note, on the site there will be a list of reports as they are created:
The reports reside on the Prey website (they are not emailed):
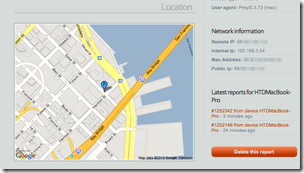
You get the Geo Location (which was very accurate actually, using just Wifi triangulation):
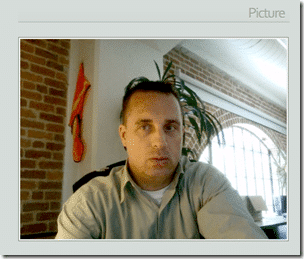
A webcam capture of the “thief” in action (do I look evil?):
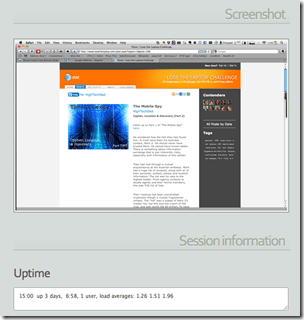
A screen capture of the active application and some session information:
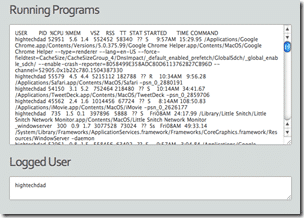
If configured, a list of running applications and the currently logged in user.
There are some other configs like Modified Files that are not shown here because I didn’t have them turned on.
When you are done with a report, you can delete it.
As far as I can tell, Prey ran pretty well. I had Little Snitch running to see if I could catch it in action and did see the program call cURL as well as a webcam capture process. Each of those items connected to the internet. You can almost “feel” when the program is running (capturing screenshots, webcam photos and other information). But other than that, it runs silently in the background.
Prey has a very small footprint (basically non-existent from a RAM perspective on Mac/Linux – only when it’s running does it suck up a minimal amount of memory & 2-3 MB RAM on Windows running as an agent). It’s pretty much impossible to remove Prey if you don’t have the administrative password. A thief could completely format your laptop I encourage you to read through some of the other FAQs which are in a tab on the homepage on how to prevent that using BIOS or firmware passwords (depending on your PC/Mac).
It’s really hard to think of a reason why you shouldn’t install Prey on your laptops. For starters, it’s really easy to install and configure. It works as described. It’s Open Source which means that there is nothing to hide in the source code. It works on multiple platforms. It is actively being developed with new features being added. It has an active community. And best of all, it’s FREE!
HTD says: Make those thieves the prey, by using Prey to tracking down your stolen laptop!